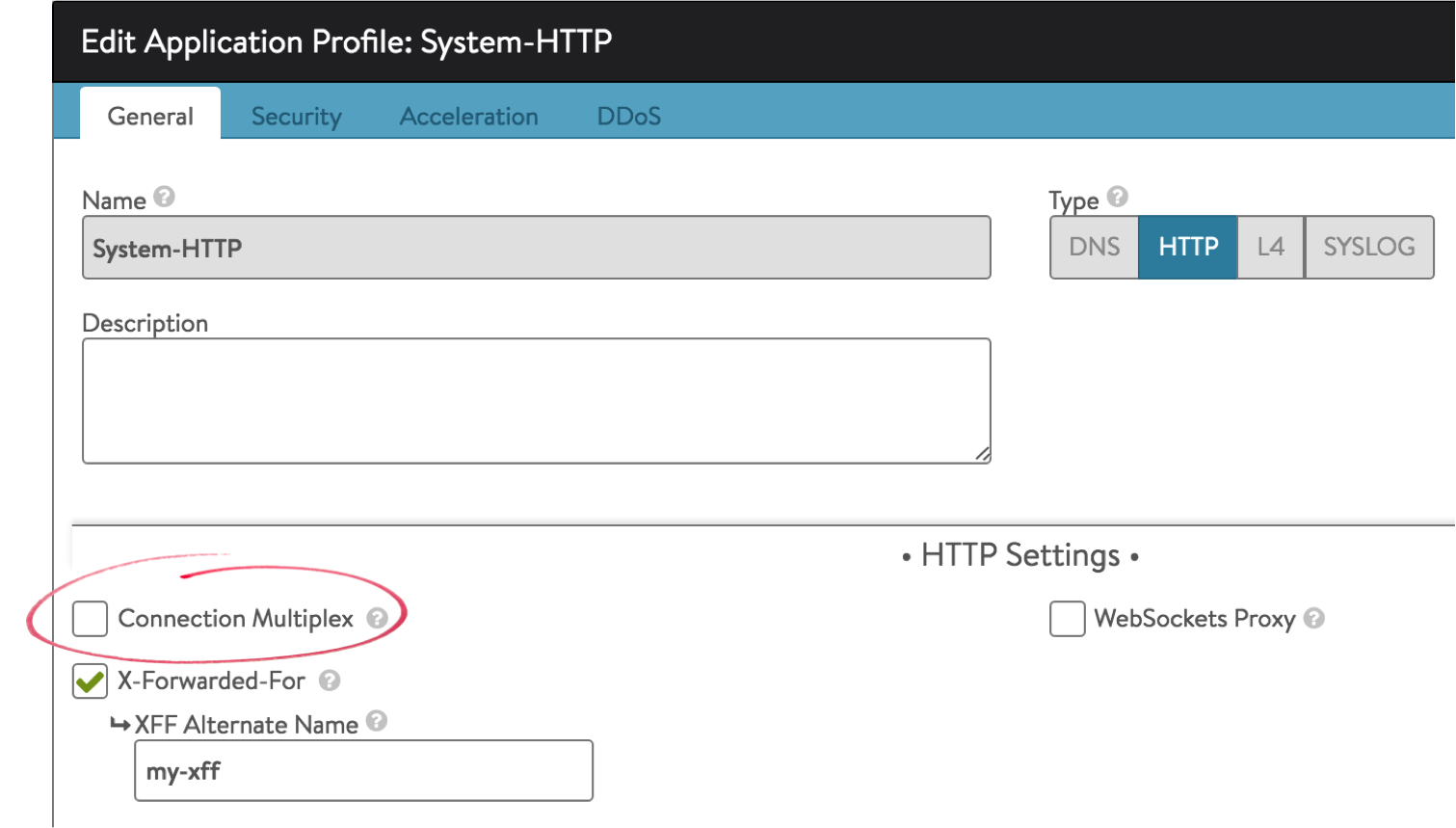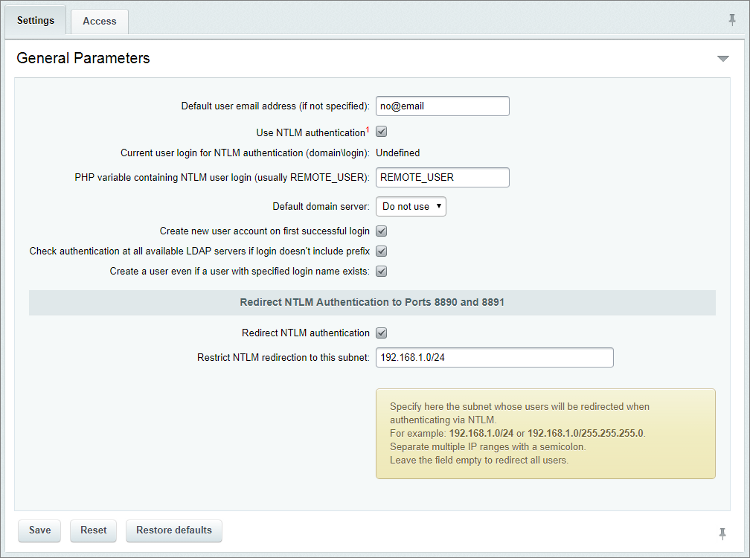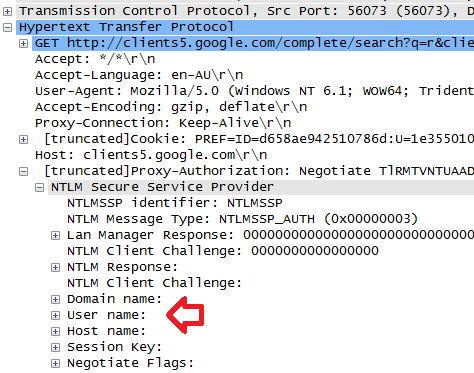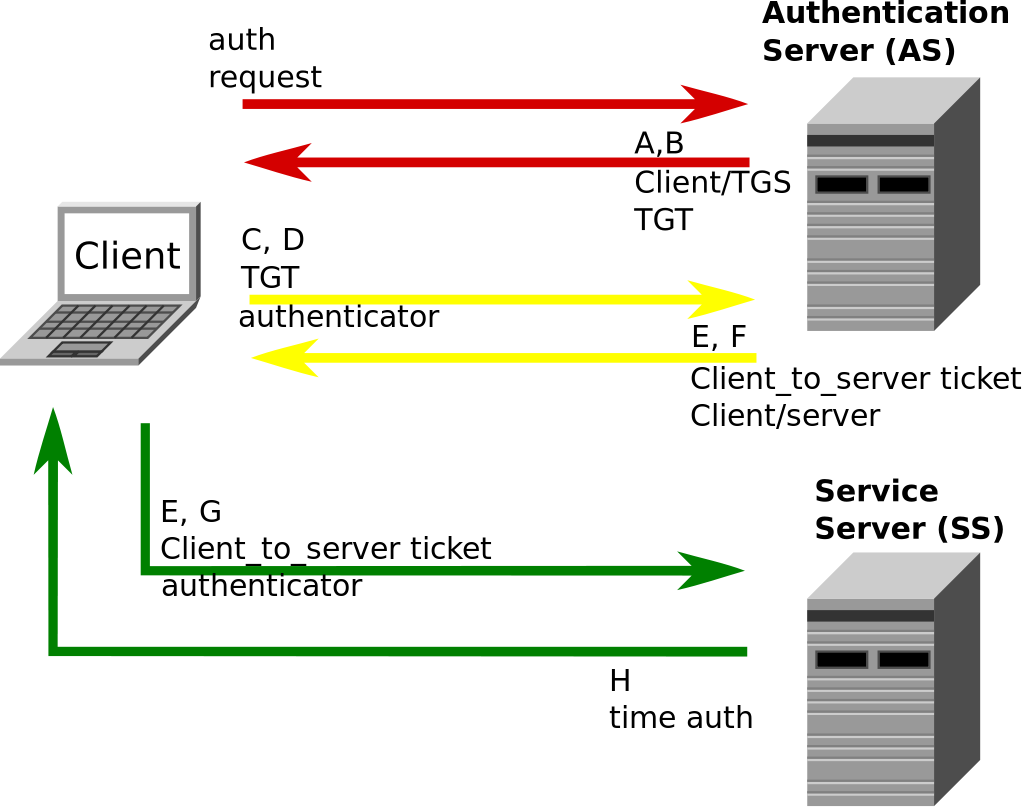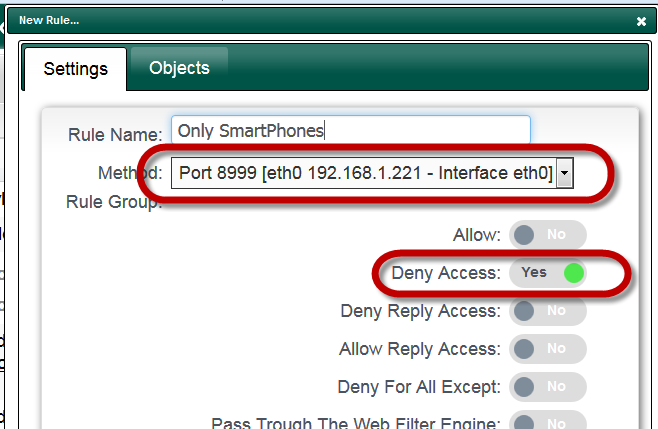
How to create a dedicated port for Smartphones in order to avoid NTLM authentication ? | Artica Proxy
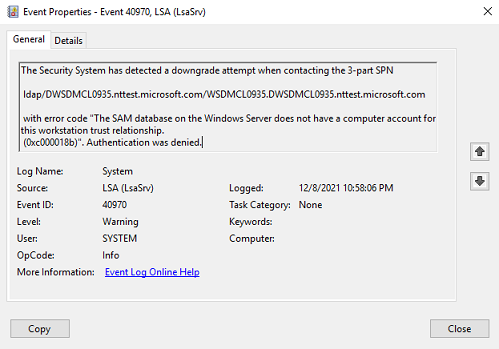
KB5011233: Protections in CVE-2022-21920 may block NTLM authentication if Kerberos authentication is not successful - Microsoft Support
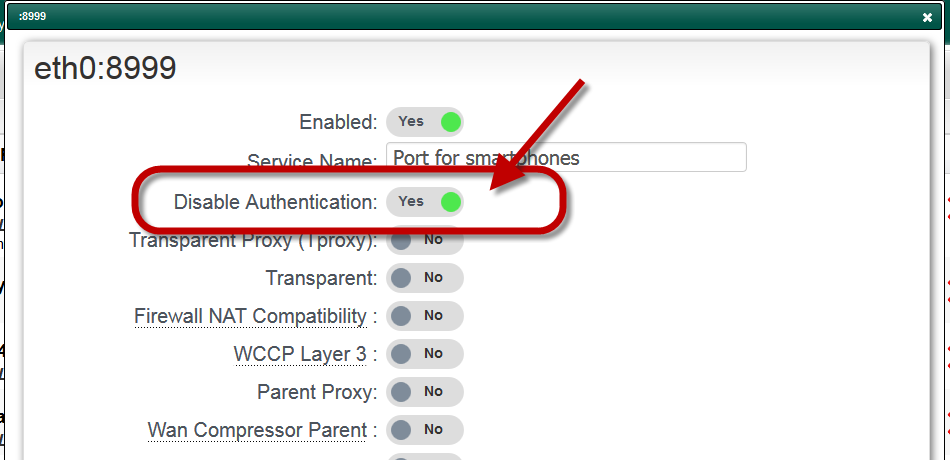
How to create a dedicated port for Smartphones in order to avoid NTLM authentication ? | Artica Proxy